Annual, bi-annual, and quarterly penetration testing schedules will be a thing of the past.
The Case for Internal and External Network Testing
In a conventional cybersecurity setup, the focus is often on safeguarding the external network, the so-called perimeter. However, this perimeter-centric approach, while essential, is not sufficient in today's threat landscape.Why? Because a data breach doesn't necessarily need to originate from an external source.
In fact, according to the Verizon 2021 Data Breach Investigations Report, internal actors were responsible for approximately 30% of data breaches. Furthermore, the attacker can freely navigate the internal network once the perimeter defense is breached, leading to potentially catastrophic damage.
This is where PTaaS shines. It presents a comprehensive approach by testing both internal and external networks. This not only helps detect vulnerabilities but also aids in architecting a network design that limits the data exposed in case of a perimeter breach.
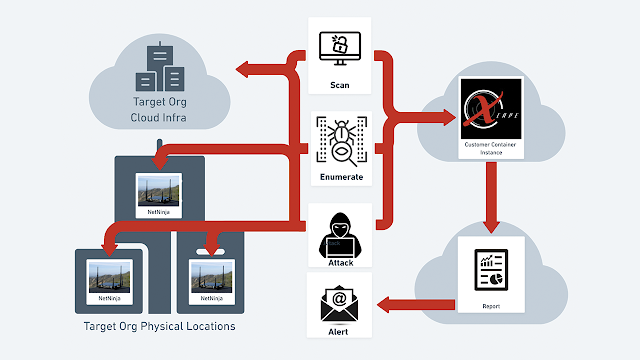
With the deployment of our specialized appliances like the NetNinja, and the PiRAT, which operate on our secure cellular network, PTaaS can continuously scan, enumerate, and pen test your network. This robust scrutiny of the external and internal network layers can expose weak points and blind spots, providing an opportunity to reinforce them before malicious entities exploit them.
From Overwhelm to Action: Prioritizing Remediation
A common pitfall with traditional penetration testing is the deluge of findings that it can unearth. While identifying vulnerabilities is a critical step, the subsequent flood of data often leaves IT teams overwhelmed and unsure of where to start with remediation.
In contrast, PTaaS offers a more manageable and efficient approach. With PTaaS, customers gain access to veteran penetration testers and blue teamers who work alongside them to sift through the findings. These experienced professionals prioritize vulnerabilities based on risk and threat actionability, providing a clear and actionable roadmap for remediation.
Rather than grappling with thousands of Jira tickets, your IT team can now focus on first fixing the most crucial vulnerabilities. This strategic, risk-based approach reduces the workload and effectively strengthens your security posture.
Scalability: The Pen Test as a Service Advantage
Penetration testing for larger organizations presents a unique challenge. The vast and often geographically dispersed network infrastructure requires the flexibility to be in more than one place at a time. Traditional pen testing methods struggle to meet this demand, often leading to inadequate coverage and overlooked vulnerabilities.
However, PTaaS, with its automated remote pen testing capabilities, offers a scalable solution. By deploying appliances like NetNinja within your infrastructure, PTaaS effectively creates a network of internal sensors that continuously scan your network. This allows for comprehensive coverage, regardless of the size or complexity of your organization.
Moreover, these sensors can work around the clock, ensuring your infrastructure is tested and monitored continuously. This significantly reduces the window of opportunity for a potential attacker, boosting your organization's overall security.
A Look at the Future: The Role of Penetration Testing as a Service (PTaaS)
As the digital threat landscape continues to evolve, it is clear that reactive approaches are no longer sufficient. Instead, a more proactive, continuous approach to security is the need of the hour, and PTaaS is leading the charge in this direction.
By leveraging the power of automation, continuous monitoring, and the expertise of seasoned penetration testers, PTaaS presents a new paradigm for vulnerability management. It's an approach that identifies and prioritizes real-time vulnerabilities and assists in timely remediation.
Moreover, PTaaS provides an invaluable benefit - peace of mind. Knowing that your infrastructure is under the continuous watch of expert penetration testers gives organizations the confidence to focus on their core business operations without the looming threat of a security breach.
Closing the Loop: Penetration Testing to Remediation
A critical aspect of PTaaS is the integration of testing and remediation. A traditional pen testing setup focuses on identifying vulnerabilities, often leaving the remediation process as a separate, disjointed activity. This can result in significant time lags between vulnerability detection and remediation, providing attackers with a window of opportunity to exploit these vulnerabilities.
PTaaS disrupts this model by integrating remediation within the testing process. With actionable insights and expert guidance, IT teams can initiate remediation activities parallel to ongoing tests. This "test and fix" approach significantly reduces the response time, thus minimizing the exposure of the identified vulnerabilities.
Harnessing the Power of PTaaS
In the face of the rising number of sophisticated cyber threats, organizations must rethink their approach to vulnerability management. While valuable, Traditional penetration testing methods cannot meet the demands of today's fast-paced, always-on digital landscape.
PTaaS represents a fundamental shift in how organizations approach vulnerability management. By combining the efficiency of automated testing, the comprehensive coverage of internal and external network testing, and the guidance of seasoned cybersecurity professionals, PTaaS provides an unparalleled solution to safeguard digital assets.
With its continuous, scalable, and integrated approach, PTaaS is not just the future of penetration testing – it's the future of cybersecurity management. As a result, the era of traditional penetration testing may indeed be dying. Still, in its place, a new, more effective, and efficient model is rising - one that promises to transform the cybersecurity landscape and provide organizations with the robust protection they need in the digital age.
Remember, the end goal of any cybersecurity strategy is not to generate an endless list of vulnerabilities but to secure your digital assets effectively. With Penetration Testing as a Service (PTaaS), businesses can achieve this goal more efficiently and confidently. So embrace this innovative service and set your organization on the path to comprehensive, continuous, and scalable vulnerability management by scheduling a free PTaaS consultation with our team!
TL;DR The era of traditional penetration testing is dead. In its place, Penetration Testing as a Service (PTaaS) offers a more comprehensive, efficient, and scalable solution for ongoing vulnerability management. By adopting PTaaS, organizations can stay ahead of the evolving threat landscape and ensure the security of their digital assets.
What is Penetration Testing as a Service (PTaaS), and how does it differ from traditional penetration testing? Thank you cloudtech
ReplyDelete