Penetration Testing as a Service is defined differently by a lot of different organizations. Paying attention to memes would suggest that PTaaS is nothing more than a glorified scanner, and that just couldn't be farther from the truth at least for our team at Xcape it was the pathway for us to provide our clients a more consistent easily reproducible work product. As a boutique information security firm making a name for ourselves as the company you call when all the other so called "experts" fail you. We needed a way to scale ourselves, watching the industry evolve from the sidelines missing out on work that we're overly qualified for, while other organizations grow loosing the quality of their work products because hackers aren't reproducible.
The first step for us was the hardware, building a hardware platform that makes it impossible for us not to get connected and configured made it so that we could work with any clients technical ability to deploy our solution in any environment, then we had to become an MVNO to provide ourselves connectivity that's totally out of band. The cell nerd in me took it a step further so that I can isolate devices within the LTE network so they only have access to each other. So our teams connection to our cellular network isn't just novel connectivity our devices we use internally are connected to the private proportion of our LTE network.
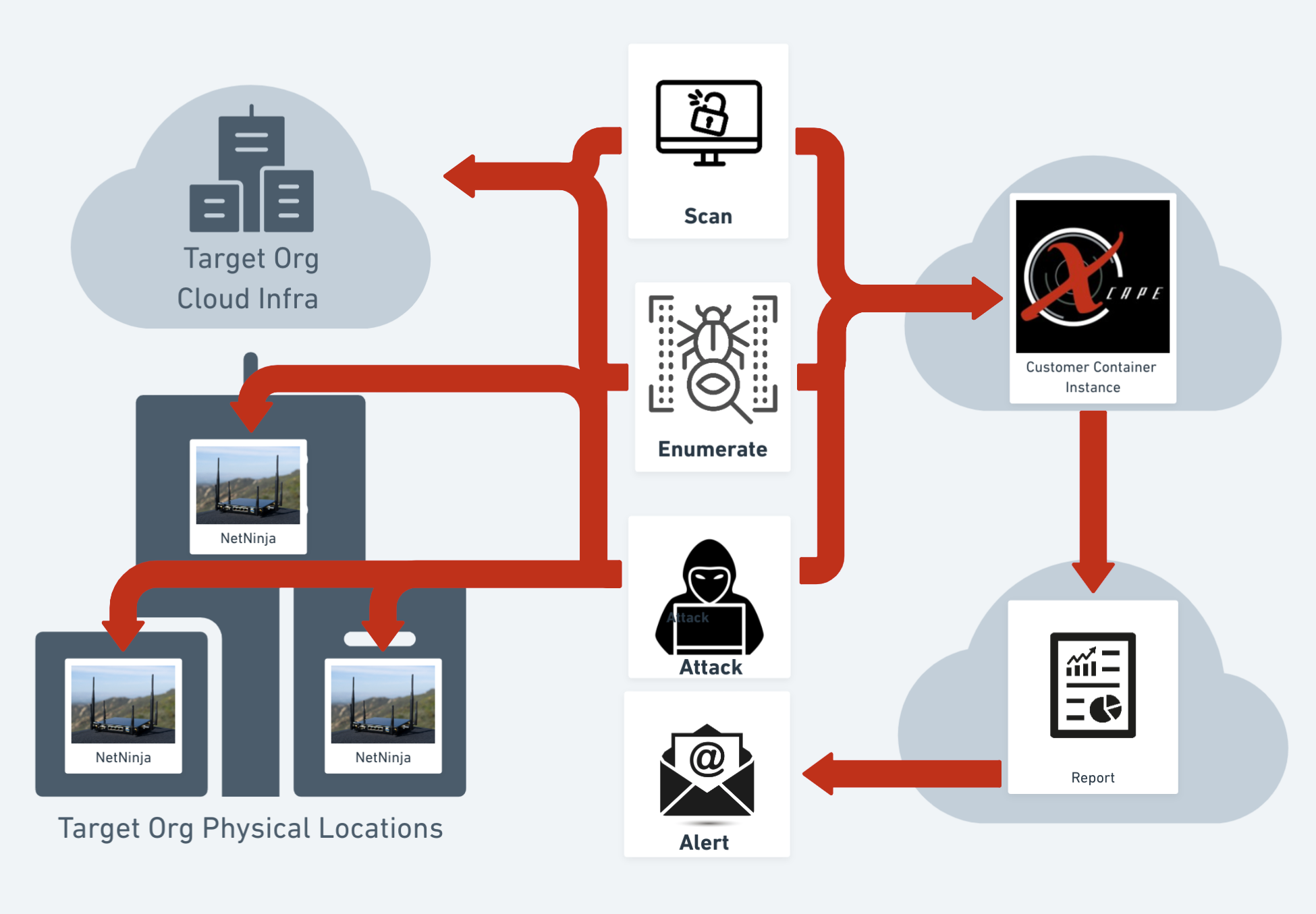
In building PTaaS we knew the goal was always to automate as much of the tedious workflow as possible. So much so that instead of pentesters being network engineers, and technical support staff on engagements, with the workflow and software we've developed, this tool means that our pen testers spend more time actually pen testing, developing malware, and discovering attack chains that lead to compromised systems, the goal of any pen test.
So what is pen testing as a service you ask? We started with automating most of the first half of our asset discovery workflow. I can't tell you how many pen test we've been on where the target list we're given ends up being just a portion of the end points they have. So our initial scan takes into account that some clients might not be aware of all of their infrastructure so our XBMAS engine does the work of doing OSINT on the client with the targeting information provided, and goes and digs up assets that are related to the organization.
Great now we know about all the assets belonging to your organization and we can start using industry leading tools that are always being updated with fingerprinted vulnerabilities, and new tactics developed internally by our team to scan your internal and external infrastructure for known vulnerabilities building an attack profile of all the exploitable systems within your internal network, external perimeter, and cloud infrastructure.
Now we've got this automated attack profile based on the results of a bunch of scans of your internal, external and cloud infrastructure. So with the help of our cloud infrastructure and our NetNinja, our system will launch automated attacks against your infrastructure, providing screenshots and code execution of working exploit code that works to gain access to your systems.
So at this phase the automation has done its job and our pentesters have shells waiting for them to dig on. That means on the majority of all our pen test, our testers are spending 100% of their time exploiting systems, working to build attack kill chains, developing malware and custom payloads. We spend more of our time working out ways to exploit your infrastructure over the longer term of our ongoing engagement.
So instead of a two week smash and grab that results in a large report with a lot of findings, you can instead work with our team to identify vulnerabilities as they're discovered, with access to our pen testers and MSP staff for escalating the remediation of vulnerabilities your team might not have the ability to address.
Anyone trying to sell you PTaaS without automated exploitation is just lying to you because that's what we call vulnerability scanning and management, which just isn't the same as pen testing.
What we define as Penetration Testing as a Service will set the bar for what the expectation should be when you talk to a firm about PTaaS. If you ain't getting hacked it's not a pen test.
Click here to learn more about PTaaS by Xcape, Inc.

Comments
Post a Comment