Penetration Testing as a Service (PTaaS) is a relatively new approach to cybersecurity that is rapidly gaining popularity. It involves using automated tools to scan networks, systems, and applications for vulnerabilities rather than relying on traditional pen testing on a schedule. As a result, PTaaS offers many advantages over conventional pen testing, including faster and more efficient testing, consistent testing, cost-effectiveness, more comprehensive testing, and scalability.
And while PTaaS may be a new approach to cybersecurity, our team at Xcape, Inc., has been developing our version for the last four years, testing it alongside ourselves on standard engagements. Our version is the most comprehensive for internal, external, and cloud infrastructure scanning because of the Xcape Blended Methodology Adversary Simulation engine, or XBMAS.
This article will explore these advantages in more detail and explain why PTaaS is becoming increasingly popular among organizations of all sizes and industries to improve their cybersecurity posture. And how our XBMAS engine makes our offering different from the competition.
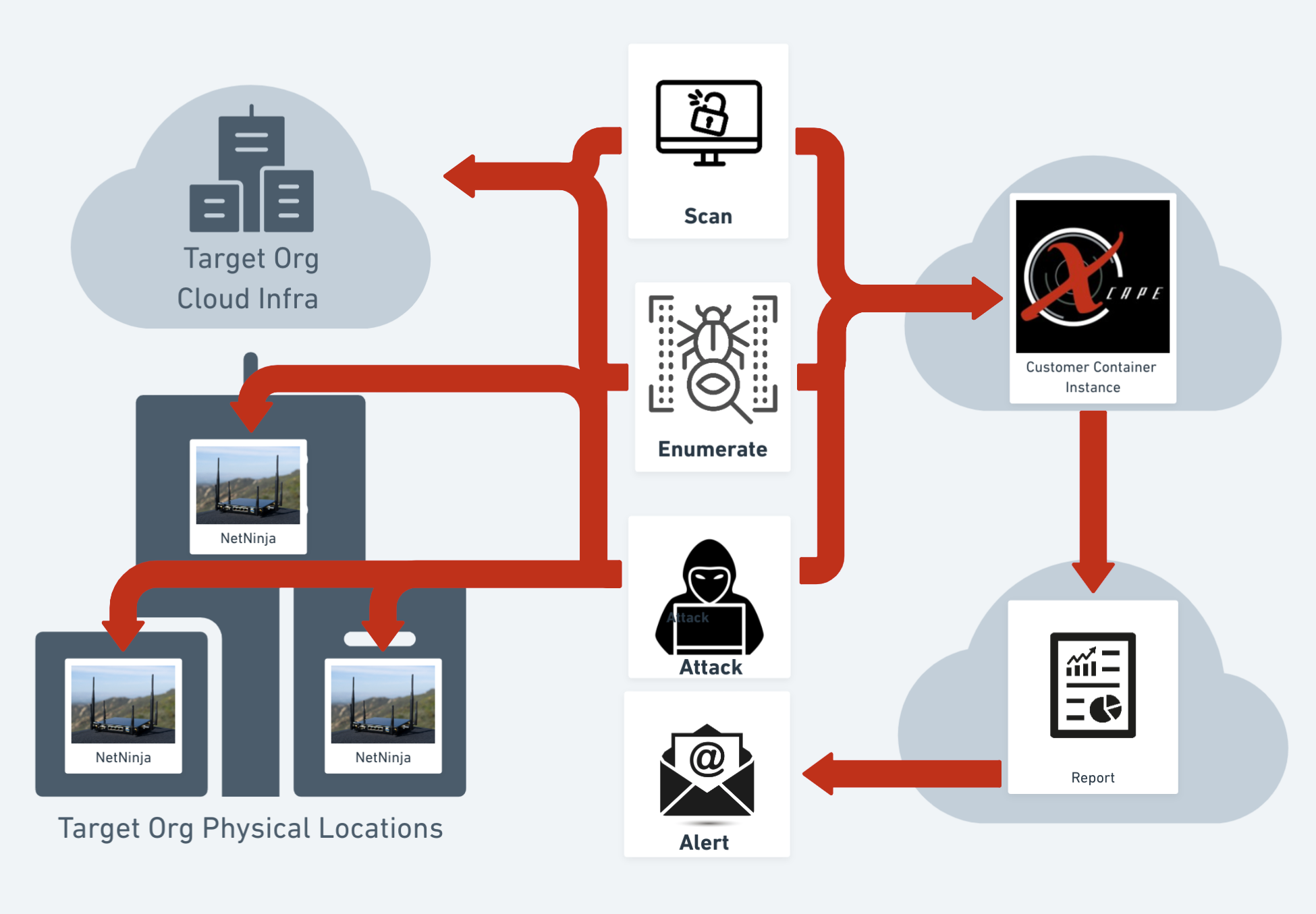 |
| PTaaS Workflow by Xcape, Inc. |
Faster and More Efficient Testing
One of the primary advantages of PTaaS is that it is much faster and more efficient than traditional testing. The automated tools used in PTaaS can scan networks, systems, and applications quickly and accurately, reducing the time it takes to identify vulnerabilities. Addressing vulnerabilities promptly reduces the window of opportunity for attackers to exploit them.
In addition, we can cover a much larger scope than manual testing using our NetNinja appliance. With it deployed in our customer's infrastructure, we can scan thousands of systems and applications across multiple sites quickly, which would be impossible for human testers to do in a reasonable amount of time. So that organizations can get a more comprehensive view of their security posture, including identifying previously unknown vulnerabilities.
Consistent Testing
Another advantage of PTaaS is that it can run consistently and continuously, which is impossible with traditional testing. Traditional pen testing is done on a schedule periodically, which means that vulnerabilities can be missed between tests. With PTaaS, scans can be run regularly as frequently as daily.
Then the data from those scans are fed to our XBMAS engine for the automated attack portion of the test. We use automation to assist our pentesters in getting their initial access to our customers' systems, allowing them to spend more time on exploit development. From there, our testers take over, attempting to validate and prove the viability and business impact of the results of our scans, ensuring that vulnerabilities are identified and addressed promptly.
Consistent testing also helps organizations meet compliance requirements, such as those mandated by PCI-DSS or HIPAA. For example, these regulations require regular vulnerability testing, and PTaaS can make it easier to meet these requirements.
Cost-Effective
PTaaS is also more cost effective than traditional testing. Traditional testing requires hiring external testers, which can be expensive, especially if testing needs to happen frequently. Our PTaaS solution uses software and hardware tools to scale our team's reach.
In addition, PTaaS can help organizations save money by identifying vulnerabilities early before they are exploited. Thus reducing the costs associated with data breaches, including the cost of investigations, remediation, and legal fees.
More Comprehensive Testing
PTaaS is also more comprehensive than traditional testing. With over 50 automated tools in PTaaS, it can scan for a wide range of vulnerabilities, including those that human testers may miss. PTaaS can also detect vulnerabilities specific to particular software versions or configurations, which can be difficult for human testers to identify.
In addition, PTaaS can help organizations identify vulnerabilities in internal and external infrastructure, third-party software, and cloud environments. This is important because many organizations rely on third-party vendors and cloud providers for critical services. Internal infrastructure vulnerabilities identified as possible pivot points in the event of a breach are also cataloged. PTaaS can help identify vulnerabilities in these environments that may not be identified through traditional testing.
Scalability
Finally, PTaaS is highly scalable, which is impossible with traditional testing. Traditional testing requires human testers, which can limit the scope of testing and the number of systems and applications that can be tested. PTaaS can be scaled to cover thousands of systems and applications, making it ideal for organizations of all sizes.
In addition, PTaaS can be customized to meet the specific needs of each organization. For example, some organizations may require more frequent scans, while others may require scans of specific systems or applications. PTaaS scans are tailored to meet these needs, ensuring organizations get the most value from their investment.
Potential Drawbacks of PTaaS
While PTaaS offers many advantages over traditional testing, it has its potential drawbacks. One potential drawback is that automated tools may only identify some vulnerabilities, especially those that are complex or require manual testing. In addition, automated tools may generate false positives or negatives. So our team of seasoned pentesters evaluates findings and retests infrastructure when these issues get identified.
In conclusion, PTaaS is a better approach than traditional pen testing on a schedule. It is faster, more efficient, consistent, cost-effective, and more comprehensive than traditional testing. As organizations continue to face an increasing number of cyber threats, adopting PTaaS can help them identify vulnerabilities and protect their networks, systems, and applications from attackers.
Want to Learn More about what PTaaS from Xcape, Inc., has to offer, Click Here
Interested in scheduling a consultation? Click Here
Comments
Post a Comment